First up:
Who’s been spoofing the FT?
FT via Alphaville:, August 17
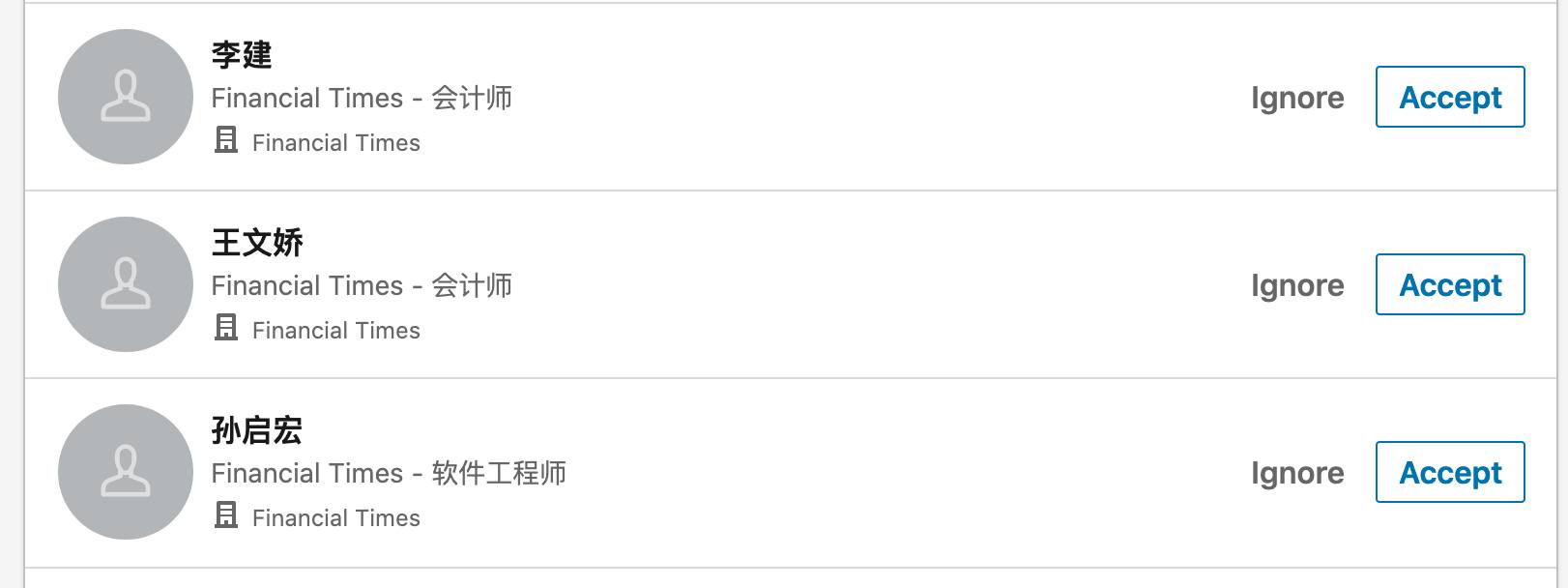
In the first few days of August, Financial Times journalists started receiving a sudden surge of LinkedIn requests from suspicious accounts.
They all looked like new accounts, with no profile pictures, no biographies, and few contacts. Their only connection was that they claimed to work for the Financial Times in China.
Izzy on FT Alphaville, for example, got these requests:
The only problem: the FT offices and roles they claim to work in do not exist. These fake accounts have generated over 170 connection requests to over 30 colleagues in the space of a week. When contacted by direct message, the accounts have failed to reply.Why do they want to know us? Journalists face many disinformation and hacking attempts, from a number of adversaries. Security researchers have long warned that Chinese state-backed hacking groups have targeted journalists with personalised phishing attempts.
In these “spear-phishing” expeditions, an attacker tries to get the victim to install malicious software, or to give up clues to passwords or security questions, using some social engineering — say, pretending to be a colleague, for example. Spear-phishing attempts easily snowball: once you get into someone’s LinkedIn network, you look more plausible to their colleagues.
This time, however, the accounts might not be after access to sensitive information. Instead, they could be trying to gather more credentials to establish their authenticity for use in a future disinformation campaign.....MORE
Editors and journalists often resort to someone’s online presence to verifying their identity. But what if it is fake from the beginning and compounds from there?
In July, Reuters discovered that Oliver Taylor, whose articles have appeared in the Jerusalem Post and the Times of Israel, was a fiction: his photo was generated by an AI deepfake algorithm. In the same month, the Daily Beast uncovered a network of at least 19 fake personas used to pitch articles to outlets from the Washington Examiner to the South China Morning Post....
Which was followed the next day by:
Linkedin FT spoofing, a forensic analysis
Since the beginning of August, Financial Times journalists have been receiving strange connection requests on LinkedIn from supposed colleagues domiciled in China. The problem, as we alerted on Monday, is that the FT offices and roles they claim to work in do not exist.....MORE, including an interesting web of connections
Many might interpret the incident as a commonplace hacking attempt. Fake Linkedin accounts, after all, are no new thing and phishing attacks are a daily occurrence in cyberspace. It’s certainly not the first time an FT journalist will have been targeted by a dodgy profile.
Yet, at the same, there seemed to be something suspiciously synchronised about the requests. And what with deepfakes on the loose and Linkedin being used in the past to solicit would-be Chinese spies, it does feel like there could be something much bigger going on in cyberspace....
There are two more of her pieces I want to get to and comment on, and some stuff on Joe Biden and Juff Gundlach.
Previously:
The Recent Work Being Done By The FT's Izabella Kaminska Is Important...
Corrected—So, What Has The Financial Times' Izabella Kaminska Been Up To?
"Cognitive hacking as the new disinformation frontier"