Operating a botnet is expensive and risky. But it’s all worth it if you’re making $20 million a month from click fraud.
Botnets are shadowy networks of computers controlled by hidden actors and linked to everything that’s bad on the web. They have been implicated in distributed denial-of-service attacks, spamming campaigns, click fraud, and bank fraud, to name just a few of the nastiest flavors of cybercrime. Clearly somebody, somewhere is making a fortune masterminding this kind of criminal activity.
But just how much money do botnets generate, and what is the business model that supports this kind of activity?
Today we get an answer of sorts thank to the work of C.G.J. Putman at the University of Twente in the Netherlands and a couple of colleagues. “It comes as no surprise that the primary motive for the use of botnets is for economic gain,” they say as they map out the costs and revenue streams.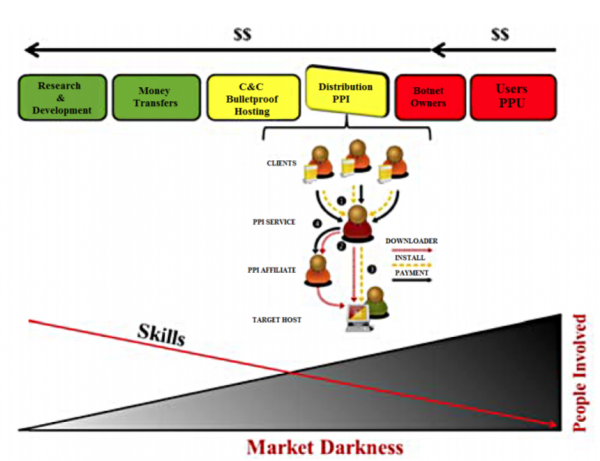
A botnet is essentially a network of computers, smartphones, or intelligent devices that can be controlled by an unauthorized attacker. The network is created by infecting each device with malware that communicates via standard network-based protocols with the controller and the other devices. The controller can then manipulate the devices within the botnet in various nefarious ways.
Of course, there are considerable costs involved in setting up such a system. The first is the research and development necessary to find loopholes in operating systems and then to write code that can exploit them.
This is a highly specialized task. Putnam and co suggest that planning and executing a botnet capable of attacking the internet infrastructure on a national or international scale would require a significant set of experts, including vulnerability analysts, exploit developers, testers, and managers—perhaps many hundreds of them in the case of a botnet set up to attack the US. This kind of system would take around two years to plan and execute.
Once the malware has been developed, it needs to be spread. Interestingly, many of the required services can be purchased easily online. For example, potential botnet masters can make use of pay-per-installation services to set up the network. These can be bought on the dark web, with a fixed fee of 2 to 10 cents per device for installing the malware.
This service probably relies on existing botnets, which is why computers that become infected with one type of malware are often soon inundated with other types.
Some web hosting operators also offer a “bulletproof” service, which is essentially a no-questions-asked form of data storage that gives customers significant leeway over what they do. That would certainly be handy for would-be botmasters.
Then there is the cost of maintaining the network once it has been established. The malware will be removed from devices at a certain rate, perhaps because the operating system has been patched or anti-malware released to combat it. On less sophisticated devices such as internet-enabled cameras, the malware can be removed by rebooting.
So the botmaster must combat this attrition by reinfecting machines at a similar rate. That might be as easy as checking IP addresses and reinfecting those that don’t respond, in the case of simple devices. But it could be significantly more complex if the malware requires code updates when patches are released.
That can be expensive. “Re-infection costs have been estimated at $0.0935 per device,” say Putman and co.
All that leads to a rough estimate of the cost of setting up a botnet on a national or international scale. For a botnet linked to 10 million devices, Putnam and co quote a cost in the region of $16 million. Of course, it could be significantly less for smaller networks.
This kind of expenditure looks huge, but it pales into insignificance compared to the rewards on offer.
Putman and co study four different business models to see how much revenue a botnet could generate. These are distributed denial-of-service attacks, spam advertising, bank fraud and click fraud.
The team say that distributed denial-of-service attacks using a network of 30,000 bots can generate around $26,000 a month. Spam advertising with 10,000 bots generates around $300,000 a month, and bank fraud with 30,000 bots can generate over $18 million per month. But the most profitable undertaking is click fraud, which generates well over $20 million a month of profit.......MORE
Ref: arxiv.org/abs/1804.10848 : Business Model of a Botnet